SlopAds Ad Fraud Campaign Exposed: 224 Apps, 38M Downloads Removed from Google Play
Researchers uncover SlopAds, a massive ad fraud scheme hidden in 224 Android apps with 38M downloads worldwide. Learn how it worked and how Google shut it down.
NEWS
Qasim
9/17/20252 min read


SlopAds: Global Ad Fraud Scheme Exploits 224 Apps, 38 Million Downloads Disrupted
A large-scale ad fraud campaign, known as SlopAds, has been uncovered running across 224 Android apps with a combined 38 million downloads in 228 countries and regions.
How SlopAds Worked
According to HUMAN’s Satori Threat Intelligence team, the apps secretly delivered malicious code through steganography and hidden WebViews, redirecting users’ devices to attacker-controlled “cashout” websites. This generated billions of fake ad clicks and impressions without users’ knowledge.
The operation was sophisticated, using AI-themed services such as StableDiffusion, AIGuide, and ChatGLM hosted on the attackers’ servers. At its peak, the campaign created 2.3 billion daily bid requests, with most traffic coming from the United States (30%), India (10%), and Brazil (7%).
Google’s Intervention
Google has since removed all identified apps from the Play Store, cutting off the threat actors’ ability to continue the scheme.
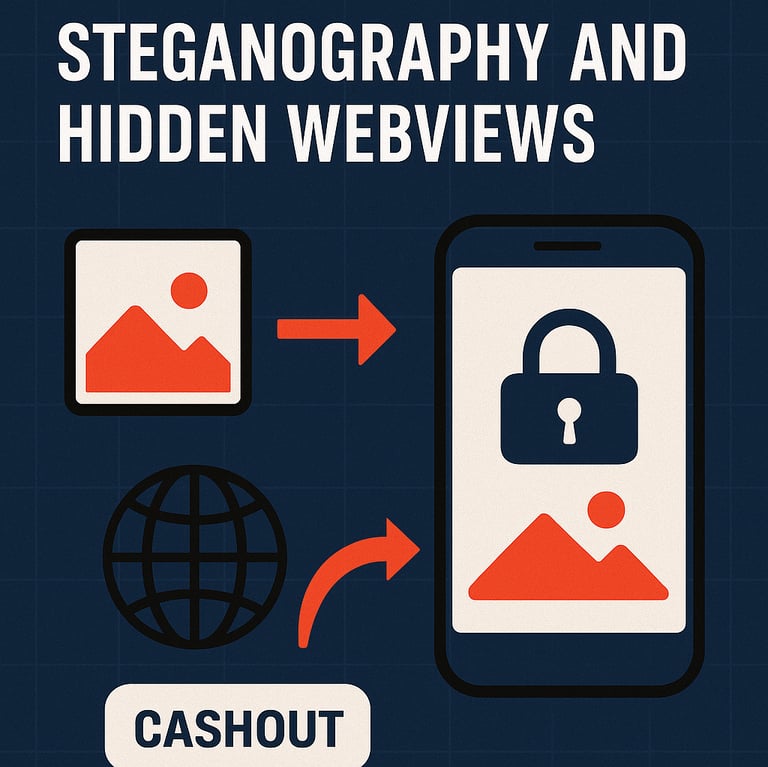
Conditional Fraud Execution
What made SlopAds unique was its conditional fraud tactics. When an app was downloaded, it first checked whether the installation came from a direct Play Store download (organic) or through an advertisement click (non-organic).
If downloaded via an ad, the app fetched a hidden fraud module called FatModule from its command-and-control server.
If installed directly, the app behaved as advertised, leaving users unaware of malicious activity.
This selective approach allowed fraud to stay hidden from security researchers, blending fake traffic into legitimate campaigns.
Technical Breakdown
The FatModule was disguised within four PNG image files containing encrypted APKs.
Once activated, it harvested device and browser information and used invisible WebViews to perform ad fraud.
Attackers funneled traffic into their HTML5 gaming and news websites, which displayed frequent ads. Because the WebViews were hidden, fraudulent clicks and impressions could be generated at scale.
Investigators also linked over 300 domains promoting SlopAds apps to a Tier-2 C2 server hosted on ad2[.]cc.
Industry Impact
The discovery comes just two months after HUMAN flagged another fraud campaign called IconAds, which involved 352 Android apps.
“SlopAds shows how mobile ad fraud has evolved, with stealthy execution and fast scalability making detection increasingly complex,” said Gavin Reid, CISO at HUMAN.
